Vaccine scams boom on the Darknet says Kaspersky
Scams are operating on the Darknet to fraudulently sell three main vaccines rolling out to the public globally.

Scams are operating on the Darknet to fraudulently sell three main vaccines rolling out to the public globally.
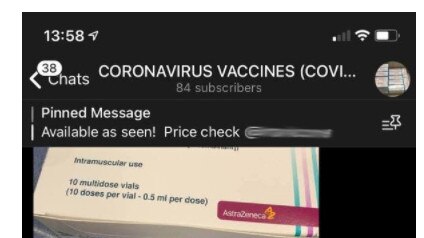
Researchers from cybersecurity firm Kaspersky said it had examined 15 different marketplaces on the Darknet and found advertisements for the Pfizer/BioNTech, AstraZeneca, and Moderna vaccines.
The Darknet is a section of the internet that is inaccessible to regular browsers. You need to use special software to connect to it and it is a haven for nefarious activity.
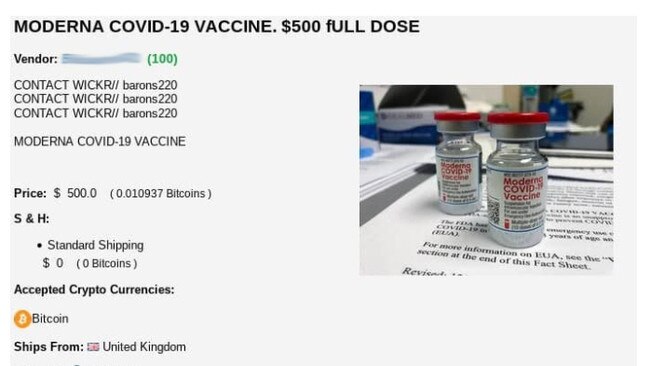
“The majority of sellers came France, Germany, the UK, and the USA, and the prices per dose ranged from $US250 to $US1,200, with an average cost of about $US500,” said Dmitry Galov, a security expert at Kaspersky.
Further analysis showed that pricing had increased significantly following publication of Moderna’s and Pfizer’s effectiveness, as did the number of advertisements.
Mr Galov said the Darknet suppliers used encrypted messaging apps such as Wickr and Telegram to communicate with potential buyers. Payments were requested in the form of cryptocurrency, primarily bitcoin.
“The majority of these underground sellers have made between 100-500 transactions, indicating that they’ve been completing sales but what exactly Darknet users are purchasing remains unclear.”
Mr Galov said it was impossible to assess whether those who paid received any vaccines or medicines, but given the special conditions needed for storing them in transit, such as -80 to -60C for Pfizer/BioNTech, it is unlikely they are valid doses.
“With the information available to Kaspersky experts, it’s impossible to tell how many of the vaccines doses being advertised online are actual doses (many medical facilities have found themselves with leftover doses) and how many advertisements are a scam.
“Even if you did receive something in the mail, most likely what you would receive would not be an effective, valid dose.”
Mr Galov said it was not surprising that sellers would attempt to capitalise on the vaccination campaign.
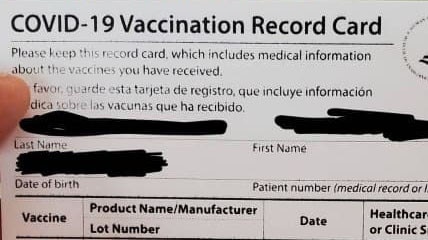
“Right now, not only are people selling vaccine doses, but they’re also selling vaccination records. It’s important for users to be cautious of any ‘deal’.”
Kaspersky in a blogpost also reported fake vaccination certificates online.
Another Kaspersky researcher, Vitaly Kamluk, said the company had been on the lookout for attempts to steal data from vaccine installations.
Mr Kamluk, director of Kaspersky’s global research & analysis team for Asia Pacific, said the company expected that cyberattacks this year might target new products, new services and new companies that appear on the market, and the vaccine was a new product. Businesses related to research and distribution were likely targets.
This week Reuters reported that Chinese state-backed hacking group APT10 had targeted two Indian vaccine makers, the Serum Institute of India and SII, a manufacturer of the AstraZeneca vaccine. Reuters said the attack was uncovered by Goldman Sachs-based Cyfirma.
“The real motivation here is actually exfiltrating intellectual property and getting competitive advantage over Indian pharmaceutical companies,” Cyfirma chief executive Kumar Ritesh told Reuters.
Three weeks ago, it was reported that South Korean intelligence had reported an attempt by North Korea to steal Covid vaccine and treatment technology from North Korea.
Mr Kamluk said the Lazarus Group with links to North Korea was the suspected culprit.
He said the World Health Organisation and vaccine research facilities in Europe also had been attacked.






