Aussie banks targeted in global cyber heist as Chinese hackers infiltrate telcos
Cyber criminals have posed as recruiters offering unsuspecting Australians bogus lucrative jobs as part of a global theft of online banking details and other sensitive data.

Australian banking apps, including the top four, have been caught in an “extremely sophisticated” global malware attack targeting android phone users.
Texas-based Zimperium – which protects the mobile devices of US troops and has built a “mobile threat defence” shield in Canberra – uncovered the attack, which involves criminals impersonating recruiters contacting unsuspecting Australians with job offers.
The Australian Signals Directorate and Australian Cyber Security Centre also warned about a separate attack from Chinese hackers, identified as “Salt Typhoon”, which infiltrated the mobile networks of a dozen companies, including in the US.
Zimperium mobile security expert Kern Smith said the attack demonstrated the increasing sophistication of network-level threats targeting telecom infrastructure.
“This breach granted them access to sensitive data such as call records, live calls and unencrypted text messages, including communications involving senior government officials and political figures,” Mr Kern said about Salt Typhoon’s attack.
The separate bank app theft involved criminals presenting victims fake job offers and then directing them to download a purported CRM android application, which eventually installed an updated variant or Antidot Banker malware.
“Our zLabs team has identified an extremely sophisticated mishing (mobile-targeted phishing) campaign that delivers malware to the user’s android mobile device enabling a broad set of malicious actions including credential theft of banking, cryptocurrency and other critical applications,” Zimperium said.
“Evidence suggests that the malware likely injects a server-controlled layout page to facilitate the theft of sensitive data from targeted banking apps.
“The injected HTML contains a fake login form tailored to harvest credentials for specific services.”
All of Australia’s big four banks were targeted as well as Suncorp, Bank of Queensland, Bendigo Bank, ING Australia, and PayPal among a host of global institutions.
“While hundreds of banks around the globe were targeted, not all were breached by this new variant of the banking trojan. It’s important to note that the issue does not stem from the banking applications themselves. The attack targets the users’ phones, exploiting vulnerabilities to steal their credentials directly,” Mr Smith said.
Zimperium said beyond the Andidot Banker malware’s ability to mimic enterprises, it also “masquerades as Chrome and TikTok apps”. It said this demonstrated its “wide-ranging target vectors, including full device takeover and application access”.
“The level of access provided the attackers could also include corporate credentials, applications and data if the device was used by the user for remote work/access for their existing employer.”
Recruiters have been increasingly using online channels, including LinkedIn and email, to contact potential candidates. Criminals have been hijacking this popular communication method and taking advantage of people looking to find better jobs.
Zimperium said the attackers behind this phishing campaign demonstrated a “remarkable level of adaptability, leveraging diverse and sophisticated social engineering strategies to target their victims”.
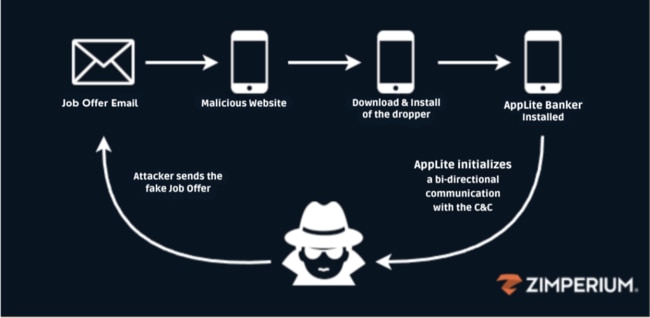
“A key tactic employed by the attackers involves masquerading as a job recruiter or HR representatives from well-known organisations. Victims are enticed to respond to fraudulent emails, carefully crafted to resemble authentic job offers or requests for additional information.
“Victims are redirected to a malicious landing page to continue the application process or schedule an interview. The landing page manipulates victims into downloading and installing a malicious dropper application.
“Once installed, the dropper delivers the AppLite banking Trojan on to the victim’s device, enabling further malicious activity.”
In regard to Salt Typhoon, Mr Smith said telcos must prioritise collaboration and adopt “AI-driven, real-time monitoring systems alongside robust mobile endpoint security solutions”.
“A comprehensive, layered approach is essential to mitigate the impact of such breaches and ensure the security of critical communications in an interconnected world,” he said.
The Australian Signals Directorate and Australian Cyber Security Centre also said more collaboration was needed.
“Visibility is critical for network defenders, particularly when identifying and responding to incidents,” the two agencies said in a joint statement.
“We encourage organisations to have ‘high visibility’ networks – meaning network defenders have detailed insight into network traffic, user activity, and data flow. This allows network defenders to quickly identify threats, anomalous behaviour and vulnerabilities.”




To join the conversation, please log in. Don't have an account? Register
Join the conversation, you are commenting as Logout