Russian ‘fake news’ evolves
A group known as Secondary Infektion used multiple languages and burner accounts to circumvent attempts to detect it, a new report says.
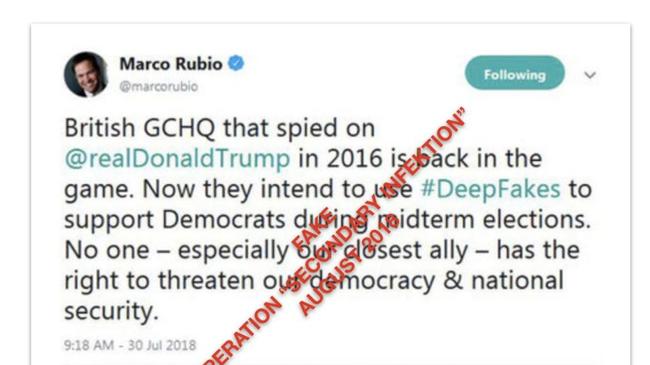
A group of Russia-based hackers used sophisticated new techniques to spread disinformation in the US and avoid detection by social media companies for years, according to a new report from an information research firm.
The findings, by the firm Graphika, could indicate how Russian efforts to spread confusion online have changed in the face of attempts to thwart them.
The group of hackers, referred to as Secondary Infektion, started six years ago and was active at least through the start of this year, Graphika said. It avoided detection by spreading its messages in seven languages across more than 300 platforms and web forums, using temporary “burner” accounts that were quickly abandoned and leaving few digital breadcrumbs for investigators to follow, said the report released Tuesday.
The group, active since 2014, was still able to operate as recently as this year, posting content such as accusing the US of creating the coronavirus in a secret weapons lab, Graphika said.
Secondary Infektion operated on popular platforms such as Facebook, Twitter, YouTube and Reddit, as well as niche discussion forums around the web, the researchers found. Using multiple platforms, while keeping its volume of activity on each low, helped the group elude the tools that social-media companies have put in place to catch such behaviour, researchers said.
Facebook, which first reported signs of Secondary Infektion in May 2019, said it was still finding and taking down the group’s previously posted content as recently as this month. However, Facebook said it sees no evidence that the group is currently active on its site.
Google, a unit of Alphabet, removed 15 inactive YouTube channels created by Secondary Infektion earlier this year, the company said.
In December, Reddit removed 61 accounts linked to the campaign, the company said. Twitter didn’t immediately respond to a request for comment.
Graphika’s report on Secondary Infektion described a variety of techniques Russia-linked groups employed to manipulate online content and adapt to growing efforts by platform companies to thwart such activity. It comes at a time of heightened concern that foreign actors may try to interfere in the 2020 presidential election in ways not unlike Russia information operations that targeted US voters four years ago.
“It would be unwise to assume that they’ve just given up and gone home,” said Ben Nimmo, director of investigations with Graphika. “The question is: ‘have they changed their tactics enough to make themselves unrecognizable?’ ”
Russia has denied interfering in the US election. The Russian embassy in Washington didn’t immediately respond to a request for comment on the findings about the Secondary Infektion campaign.
Technology companies have stepped up efforts to police their platforms after they drew fire for not doing enough to crack down on misinformation campaigns around the 2016 US presidential campaign. They have hired security researchers and built automated tools to weed out fake accounts. And they have collaborated with researchers and academics to unearth the latest disinformation campaigns.
Facebook, in the blog post spotlighting first identifying the Secondary Infektion campaign, linked it to Russia, but didn’t connect it to a specific entity or government agency. The group’s efforts match those of known information operations that were backed by the Russian government, Graphika said.
Camille Francois, the chief innovation officer at Graphika, said that by operating with “high operational security,” Secondary Infektion was able to evade detection for longer than other Russian influence operations. She called the campaign “difficult to comprehensively uncover.”
But the group’s efforts to cover its tracks came at a price. Secondary Infektion struggled to win a large online audience for its messages. The majority of the more than 2,500 posts made by the people behind the campaign were largely ignored, including 47 relating to the 2016 US election, Ms Francois said.
Congressional investigators have previously found Russian interference in the 2016 election. Those efforts included activity by a Russian firm, called the Internet Research Agency, that ran a far-reaching social media disinformation operation. Federal authorities also linked cyberattacks and leaks orchestrated against members of the Democratic Party to one of Russia’s intelligence services.
Graphika’s report into Secondary Infektion shows that the interference efforts may have been even more widespread than previously reported, even as it underscores that all such efforts don’t necessarily have a massive impact, said Thomas Rid, a professor at Johns Hopkins University who studies disinformation.
Secondary Infektion also specialised in potentially more explosive information, publishing fake documents online that it claimed were blockbuster leaks from real sources, something that it did with unprecedented persistence, Ms. Francois said. It may still be active, she said. The Internet Research Agency was focused more in creating memes, online images aimed at stirring controversy.
Aspects of Secondary Infektion’s operations have been detailed previously, but Graphika’s report is the first to trace its activities back to 2014 and to show the group’s involvement in the 2016 presidential campaign, the research group said.
Efforts by social-media companies to more effectively spot information operations in the wake of those elections may have spurred Secondary Infektion to change tactics, Graphika said. Starting in 2016, the group tightened operational security and essentially stopped posting documents from the same accounts.
And many of its messages may have failed to take off because of sloppiness that belied Secondary Infektion’s operational sophistication. Many posts were outlandish or contained obvious mistakes which discredited them. In a letter purportedly written by the Director General of the Swedish Defence Research Agency Jan-Olof Lind, the director’s surname name was misspelled as Lindt. “Maybe if they’d learned to spell the names of the politicians they were impersonating, it might have gone a bit better,” Mr Nimmo said.
The Wall Street Journal



To join the conversation, please log in. Don't have an account? Register
Join the conversation, you are commenting as Logout