Hacker group Lapsus$ attacks Okta, Microsoft, Nvidia & Samsung. Who’s next?
Newcomer hacking group Lapsus$ has proved to be a headache for Okta, Microsoft, Nvidia and Samsung. Who is next?

Newcomer hacking group Lapsus$ has already proved a headache for Okta, Microsoft, Nvidia and Samsung. The group, allegedly grounded in the UK and South America, is targeting big tech and, unlike others, boasts about its conquests by publishing screen shots and code it has stolen online. It even publishes recruitment notices.
Lapsus$ activity this week has seen authentication services firm Okta grapple with the embarrassment of dealing with a breach that potentially impacted 355 companies that use Okta login authentication and other services. That issue has turned into a PR disaster with Okta fending off criticism that it should have been open about a January incident that has come to public light now.
Microsoft, in a lengthy blogpost, has said it too had fallen victim to a Lapsus$ hack, but only a single account had been compromised. It has published a disturbing profile of Lapsus$, which uses sophisticated techniques to break into corporate systems.
Early this month GPU-maker Nvidia said it had been attacked by Lapsus$. Nvidia subsequently wanted to adopt a zero-trust structure where no employee is trusted, according to one report.
Samsung too had been breached with the group publishing snippets of code including biometric authentication information and source code from both Samsung and Qualcomm, a supplier, according to Threat Post.
The Okta breach is compounded by the company being one of the world’s most trusted providers of secure login and authentication, servicing thousands of companies worldwide.
Okta’s investigation and timeline of the January 2022 compromise: https://t.co/qq9VHpYFat
— Okta (@okta) March 23, 2022
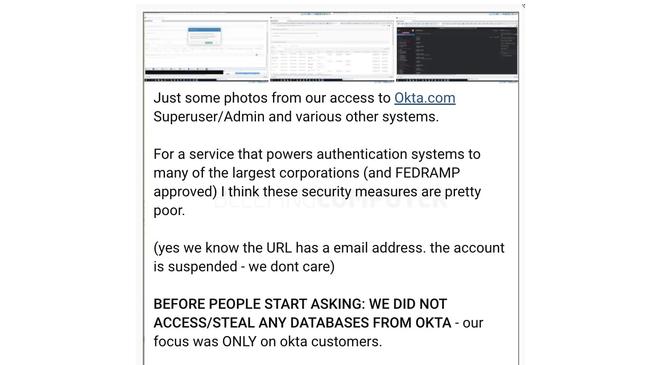
The breach became widely known this week when Lapsus$ published screenshots of its alleged activities.
Okta chief security officer David Bradbury in blogposts said the suspected breach began with a supposedly unsuccessful attempt to compromise the account of a support engineer working for one of its customers, Sitel, in January 2022.
However a report Okta received almost two months later highlighted there was a five-day window between January 16-21, 2022, where an attacker could have gained access to the support engineer’s laptop. This was consistent with the screenshots.
Mr Bradbury, in his blog posts, said Okta had concluded that a small percentage of customers, about 366, could be potentially impacted and those firms had been contacted.
However, the explanation didn’t satisfy some who said other customers should have known about the initial potential breach in January, not two months later when Okta received its report.
Mr Bradbury has blamed Sitel for a delay in providing its report. He released a timetable that said Okta had shared “indicators of compromise” with Sitel on January 21. Sitel then told Okta it had retained outside support from a leading forensic firm to investigate.
However Sitel didn’t share its summary of findings with Okta until March 17, with the full report presented on March 22 according to the timeline.
“I am greatly disappointed by the long period of time that transpired between our notification to Sitel and the issuance of the complete investigation report,” said Mr Bradbury.
But even that concession didn’t satisfied critics as the issue didn’t flare publicly until five days after Okta received the Sitel summary report. By that time, Lapsus$ had published its screenshots.
“Upon reflection, once we received the Sitel summary report we should have moved more swiftly to understand its implications,” Mr Bradbury said in the post.
He again pointed the finger at Sitel. He said Okta’s investigation had found that the screenshots, which were not contained in the earlier Sitel summary report, were taken from a Sitel support engineer’s computer “upon which an attacker had obtained remote access”.
“This device was owned and managed by Sitel. The scenario here is analogous to walking away from your computer at a coffee shop, whereby a stranger has (virtually in this case) sat down at your machine and is using the mouse and keyboard,” Mr Bradbury wrote.
“So while the attacker never gained access to the Okta service via account takeover, a machine that was logged into Okta was compromised and they were able to obtain screenshots and control the machine through the RDP session.”
While Okta continues to dissect this incident, Microsoft has revealed it has also grappled with Lapsus$, but it said an attack allegedly by the group had only compromised “a single account”.
“No customer code or data was involved in the observed activities,” said Microsoft.
“Our investigation has found a single account had been compromised, granting limited access.
“Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity.”
In its blogpost, Microsoft presented a chilling profile of Lapsus$, also known as DEV-0537. It said those behind the hacking group sought to gather knowledge about their target’s business operations, including intimate knowledge about employees, team structures, help desks, crisis response workflows, and supply chain relationships.
“Microsoft Threat Intelligence Centre assesses that the objective of DEV-0537 is to gain elevated access through stolen credentials that enables data theft and destructive attacks against a targeted organisation, often resulting in extortion. Tactics and objectives indicate this is a cybercriminal actor motivated by theft and destruction.”
It said the hacker group sometimes targeted people’s personal accounts and from there gained access to corporate networks.
“Given that employees typically use these personal accounts or mobile phone numbers as their second-factor authentication or password recovery, the group would often use this access to reset passwords and complete account recovery actions.
“Based on observed activity, this group understands the interconnected nature of identities and trust relationships in modern technology ecosystems and targets telecommunications, technology, IT services and support companies – to leverage their access from one organisation to access the partner or supplier organisations.
“They have also been observed targeting government entities, manufacturing, higher education, energy, retailers, and healthcare.”
Website security company Cloudflare, an Okta customer, has also been investigating the Okta hack but doesn’t believe it has been affected by it.
Internet 2.0 CEO Robert Potter said the fact Lapsus$ was grounded in the UK and South America meant participants were more likely to be caught by authorities compared to groups operating from Russia or China.
Some reports suggest a teenager is heading Lapsus$ operations.



