Two-factor authentication calls compromised
Android malware is capable of intercepting two-factor authentication phone calls, security firm Symantec says.
Android malware is capable of intercepting two-factor authentication phone calls, making it possible for hackers to circumvent what was thought to be highly secure connectivity, says Symantec.
The security firm in a blogpost said it had detected an update to the Android. Bankosy financial Trojan which lets malware steal passwords from voice call-based two-factor authentication.
Should an attacker know your first factor login details, they can arrange to have your second factor authentication call silently forwarded to them and complete the authentication themselves, Symantec says.
“Once installed, the malware opens a backdoor that enables unconditional call forwarding and silent mode on the device so the victim is not alerted during incoming calls.
“Once this is set, the attacker — who has already stolen the victim’s credentials (the first factor in two-factor authentication) — can steal authorisation tokens from voice calls and initiate a fraudulent financial transaction.”
Businesses and corporations are increasingly using two factor authorisation to beef up security and reduce reliance on staff using often overly simple and easily compromised passwords.
However using voice calls as the second authentication step may prove less secure than thought, and not a good second step option compared to other forms of verification such as biometric identification options like fingerprint recognition.
Symantec in a blogpost said that in the last quarter of 2015 it had observed an emerging trend among financial Trojans of added functionality to its code to enable it to deceive two-factor authorisation (2FA) systems that use voice calls. Previously this had been observed for 2FA using SMS.
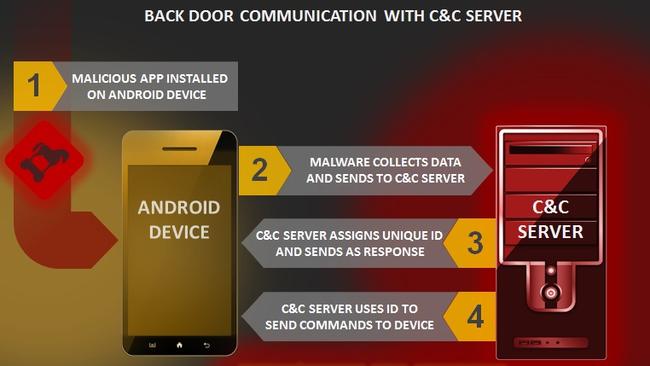
“Once the malware is installed on the victim’s device, it opens a backdoor, collects a list of system-specific information, and sends it to the command and control (C & C) server to register the device and then get a unique identifier for the infected device,” Symantec said.
“If the registration is successful, it uses the received unique identifier to further communicate with the C & C server and receive commands.”
Symantec said the malware supported call forwarding and support for disabling and enabling silent mode, in addition to locking the device, so that the victim is not alerted during an incoming call.
Symantec security specialist Nick Savvides said that in the Asia-Pacific region, hackers had successfully compromised second-factor authentication with SMS messages. He said Australian banks had fallen victim to this.
He said there was no obstacle standing in the way of hackers rerouting authentications sought with phone calls instead of SMS.
He said the attackers first sought to obtain usernames and passwords from individuals and, where successful, would seek to send them emails that when opened would give them access to their Android phone. They could comprise a phone when it was attached to an infected laptop by cable.
Hackers could then satisfy both steps of authentication.



To join the conversation, please log in. Don't have an account? Register
Join the conversation, you are commenting as Logout