Hacker linked to Ashley Madison breach previously ‘compromised’ Australian Parliament website
A TWITTER user that has previously threatened the Australian Parliament website has been linked to the Ashley Madison hack.
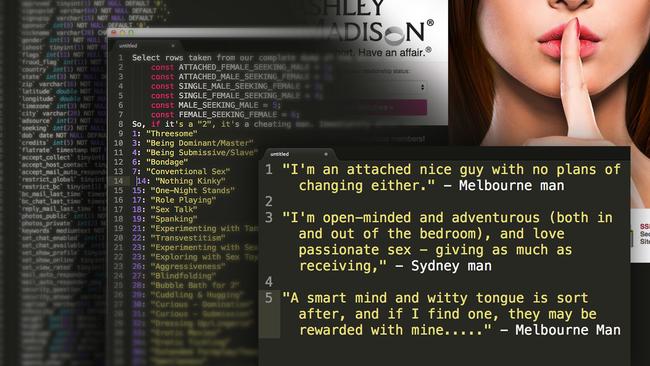
A HACKER potentially involved with the Ashley Madison leak may have been exposed and has previously compromised the website of the Australian parliament.
The allegation was put forth by investigative computer security journalist Brian Krebs and comes just a day after Avid Life Media (the company that owns Ashley Madison) offered a $523,000 bounty for information that identifies the culprits.
A group calling themselves the Impact Team have taken responsibility for the hack but at this point in time the group’s members remain faceless. However this could be the first chink in the armour.
In an article posted to his blog, Mr Krebs accused Twitter user Thadeus Zu of being involved and believes he’s unintentionally left incriminating evidence.
The user of the account is a prolific tweeter and sometimes posts hundreds of messages a day. Suspecting his involvement, Krebs downloaded the Twitter feed and sifted through it for clues.
Among them is a bizarre tweet he directed at the Australian Parliament in 2012 after he “compromised” the website of the Australian Parliament, according to the post. The tweet contained the lyrics of Aussie band ACDC’s hit song, Thunderstruck: “Parliament of Australia (dead link) Oi! Oi! Oi!….T. N. T. Dynamite! Listen to ACDC here,” it read.
It’s been revealed that the song played in the background of a message left by hackers on a staffer’s computer at Ashley Madison informing them of the breach.
Following the tweet to the Australian Parliament, he tweeted a similar message to a computer security company in the Netherlands. “Next time, it will be Thunderstruck. #ACDC,” Zu wrote.
Before the news of the hack was public, Zu was tweeting to others about getting “the show started” and a screenshot posted by the user showed a tab with the song playing on YouTube.
The user’s account boasts a number of previous smaller hacks involving the hijacking of routers, networked cameras, printers and websites.
Brian Krebs claims to be the first to know about the hack after the Impact Team contacted him on July 19 and confidentially shared a link directing him to the cache of stolen data. It was minutes later that he noticed the Twitter user also posted a URL to the hacked information. It was this that initially piqued his suspicion.
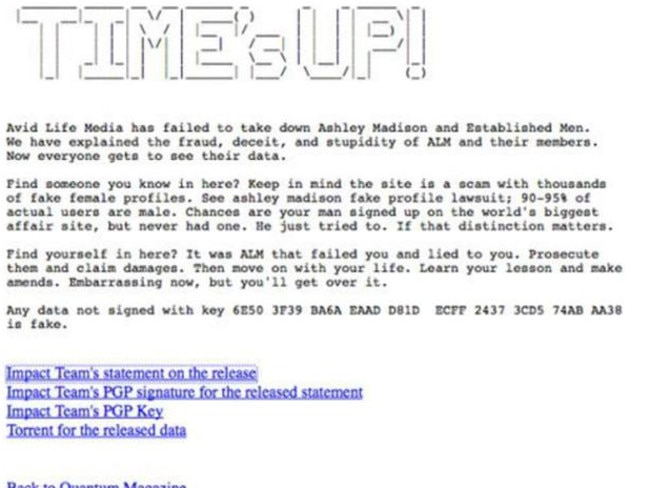
Another thing that led Krebs to believe the person was involved was when Zu posted a copy of the team’s “time’s up” statement that announced the leak of the data a full 24 hours before many journalists had begun reporting on it.
In countless tweets Zu denies involvement with the hack but frequently uses the royal “we” when referring to the hack, the blog post states.
According to the author, whoever he or she is in real life, it seems overwhelmingly likely they were somehow linked to the attack.
“It is possible that Zu is instead a white hat security researcher or confidential informant who has infiltrated the Impact Team and is merely riding on their coat-tails or acting as their mouthpiece,” Krebs wrote. “But one thing is clear: If Zu wasn’t involved in the hack, he almost certainly knows who was.”
The Toronto Police Service is leading the investigation of the data leak — which has been linked to two suicides in the country — and have enlisted the top cyber investigators in the FBI and other US agencies.



