China hackers RedEcho accused of targeting India electric grid
As tensions flared around China’s border with a domestic rival, malware began flooding into the country, until the lights went out.
Chinese hackers have been accused of causing a blackout in India’s most populous city last year after a US cybersecurity firm linked them to the incident.
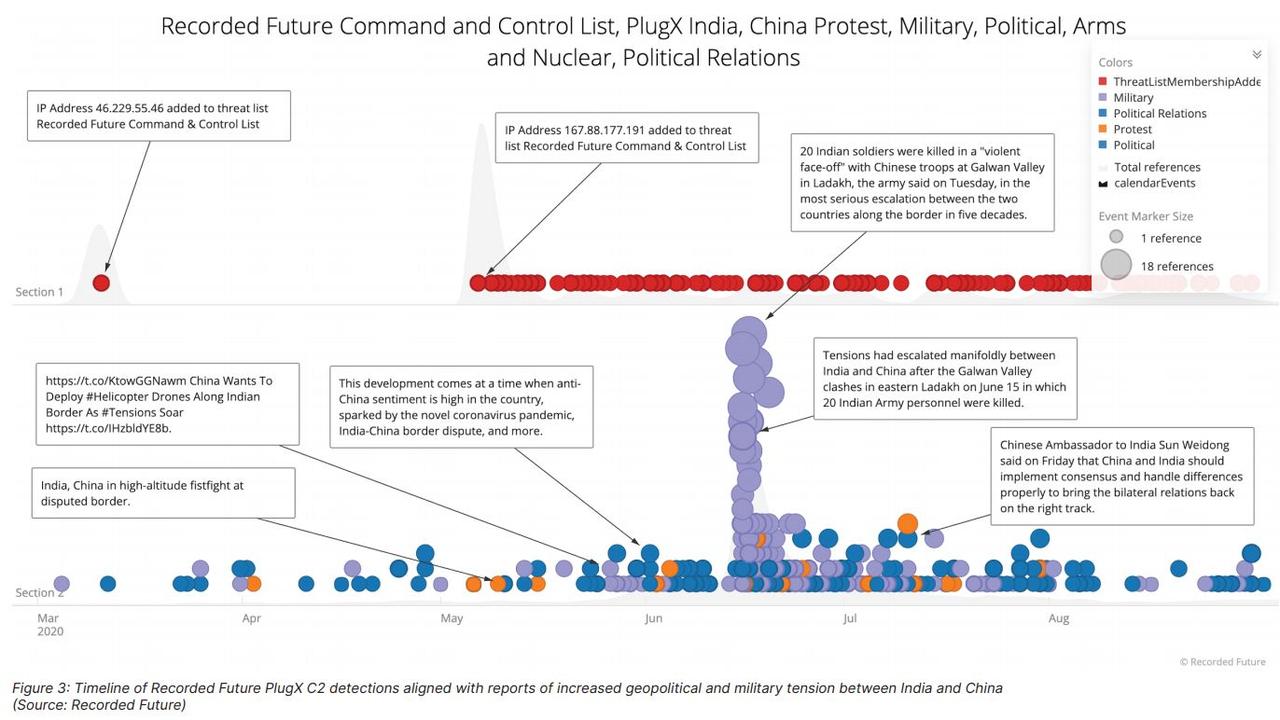
Researchers at Recorded Future recently published a report alleging a group called RedEcho said they were linked to China was “targeting the Indian power sector”.
RELATED: Woman dies after hospital hacked

RELATED: Fashion house sues Insta account for $867m
The report begins by noting that “relations between India and China have deteriorated significantly” following clashes along their border beginning in May last year, and the accusation that a group linked to China may have turned the lights out in Mumbai hasn’t helped.
“As (a) staunch defender of cyber security, China firmly opposes and cracks down on all forms of cyber attacks,” China’s Ministry of Foreign Affairs spokesman Wang Wenbin said last week.
“Speculation and fabrication have no role to play on the issue of cyber attacks, as it is very difficult to trace the origin of a cyber attack,” Mr Wenbin claimed, adding it was “highly irresponsible to accuse a particular party when there is no sufficient evidence around”.
Recorded Future notes “the alleged link between the outage and the discovery of the unspecified malware remains unsubstantiated”.
RELATED: New way kids are ditching school
RELATED: Brothers’ alleged $19m Amazon scam
The alleged link is based on a number of factors, including a “noticeable increase” in malware targeting Indian organisations in May last year, when skirmishes at the border also heated up.
The specific malware, PlugX, is not exclusive to China but has been “heavily used by China-nexus groups for many years”.
Recorded Future also “identified a heavy focus on the targeting of the Indian government and private sector organisations by multiple Chinese state-sponsored threat activity groups” throughout the rest of 2020.
The firm said the targeting of critical infrastructure in India offered “limited economic espionage opportunities”, but there was concern over “potential pre-positioning of network access to support Chinese strategic objectives”.
RELATED: Porn pauses teen hacker’s hearing

RELATED: Building hiding China’s secrets uncovered
Some Indian officials blamed China at the time of the blackout and Recorded Future noted local media had previously linked the Mumbai blackout to malware on infrastructure that balanced electricity supply with demand at load dispatch centres around India.
Recorded Future suspects RedEcho targeted 80 per cent of the regional dispatch centres and a further two state dispatch centres, as well as a high-voltage substation and coal-fired power plant.
It also accused the group of targeting two seaports.
Last week, according to Bloomberg, the hackers still had access to at least one of those ports, despite the firm’s warnings.
The Indian government was informed before the release of the Recorded Future report, as is commonplace, but the government there has yet to release its own report after being made aware of the problem on February 10.
When news.com.au went to check with the Indian Computer Emergency Response Team on Monday afternoon, its website was down.
RELATED: Hackers stole Australian defence data
RELATED: Kim’s hacker pack tried stealing vaccine
According to The New York Times, retired Indian Army cyber expert Lieutenant General D.S. Hooda said the blackout could be China “sending a warning to India that this capability exists”.
Gen. Hooda added India hasn’t “been able to get rid of our dependence on foreign hardware and foreign software”.
The Mumbai blackout in October last year included outages of up to 12 hours in some areas.
Train services were cancelled, a stock exchange was forced to stop trading, and generators were called into hospitals.
While China has been accused of increasingly carrying out cyber attacks on foreign countries, it didn’t invent them.
Russia, North Korea and Iran are all believed to be prolific in the space, and alongside China form the focus of Recorded Future’s Insikt Group that targets state-based cyber actors.
The United States and Israel have also been accused of cyber attacks, perhaps most notably by using a computer worm called Stuxnet to target Iranian nuclear enrichment facilities in 2009 and 2010, instructing centrifuges to speed up until as many as 1000 of them destroyed themselves.



