‘Breathtaking’: Genea cyberattack reveals stunning Australian problem
Countless Australians have been impacted by a truly chilling crime in the past few weeks – but nobody seems to care.
Medical records are a person’s most sensitive data.
Many Australians would be shocked to know how few regulatory protections are in place for that data.
A recent hack of a major Australian IVF clinic has perfectly demonstrated the risks of what can happen when a hacker group sets their sights on the healthcare system.
On February 14, Genea’s computer systems were hacked, taking phone lines of one of the most popular fertility services offline, disrupting patients’ IVF cycles, and yielding the thieves almost one terabyte of highly sensitive patient data, including medical records, doctors’ notes and IDs.
It’s believed that the ransomware group Termite was in the company’s systems for weeks, with its presence first detected on January 31.
Genea didn’t inform patients of this hack until February 19, and didn’t release a full list of data taken from its “folders” until the 24th.
On February 26, Genea revealed that the data had been published on the dark web.
According to the cybersecurity experts we spoke to for this story, time is of the essence in these kinds of attacks.
For patients needing to protect their identities and protect against blackmail, it’s hours that matter, not weeks.
Experts we’ve spoken to say it’s unlikely Genea will face any particularly serious consequences. Furthermore, there is no law specifying how securely medical data needs to be kept, beyond vague instructions of “securely”, leaving it up to each private healthcare company to decide how much of its company profits they want to spend on protecting patient data from cyber attacks.
According to a spokesperson for the Office of the Australian Information Commissioner (OAIC), “The Privacy Act requires organisations to take reasonable steps to protect personal information they hold from misuse, interference and loss, as well as unauthorised access, modification or disclosure. The Privacy Act is a principles-based and technology-neutral law – it does not prescribe specific steps organisations should take or methods they should use.”
Professor Sanjay Jha, a cybersecurity and privacy researcher at UNSW, told news.com.au: “Cybersecurity comes at a cost, and most businesses, if not all, are into making profit. So definitely they would [take the most cost- effective interpretation of data protection laws].”
Genea, which was bought by private equity firm Liverpool Partners in 2022, has refused to answer questions about whether the patient data was encrypted. It also has not specified whether multi-factor authentication was in place for accessing the “folders” where the sensitive data was kept.

The data taken from Genea was essentially a wish list for ransomware hackers, identity thieves and blackmailers. Roughly one in 17 births in Australia is an IVF birth, and it’s estimated that around 80 per cent of people seeking IVF treatment in Australia use one of the big three clinics, including Genea. It’s a clinic known for servicing the rich and famous, as well as everyday Australians, with clinics in every Australian state and Canberra. Genea was also in the news last year as patients looked for answers after embryos were contaminated with bacteria.
Now, patients who used the clinic as far back as six years ago have had the following kinds of data leaked onto the dark web, with Genea saying in a statement on February 24: “The folders on the patient management system include the following types of your information: Full names, Emails, Addresses, Phone Numbers, Medicare Card Numbers, Private Health Insurance Details, Defence DA number, Medical Record Numbers, Patient Numbers, Date of Birth, Medical History, Diagnoses and Treatments, Medications and Prescriptions, Patient Health Questionnaire, Pathology and Diagnostic Test Results, Notes from Doctors and Specialists, Appointment Details and Schedules, Emergency Contacts and Next of Kin, although the information differs for different individuals.”
Essentially, it’s everything except financial details, which appear to have been kept more securely.

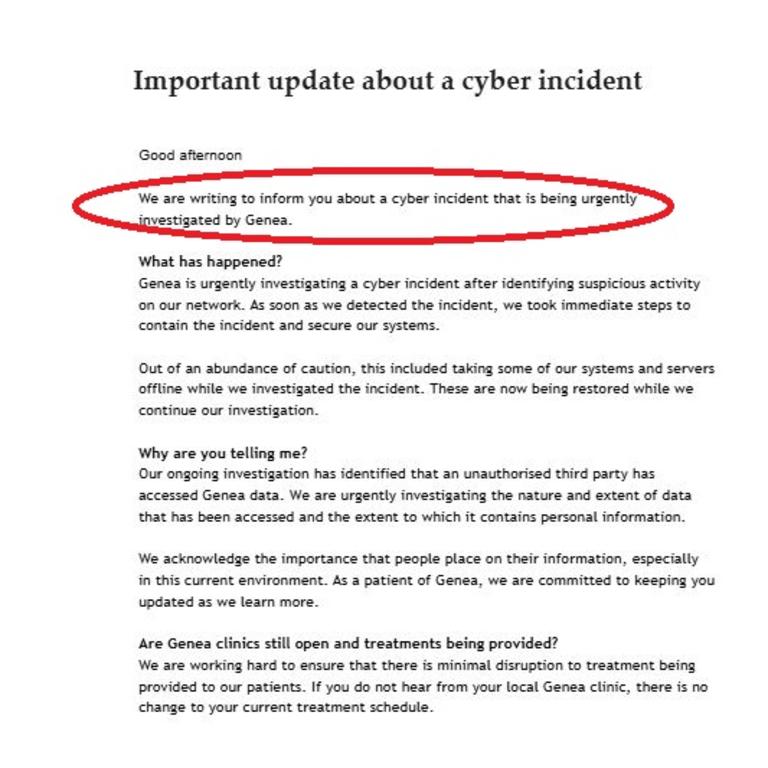
In a statement, a spokesperson for Genea told news.com.au: “Our ongoing investigation into the cyber incident has identified that data taken from our systems has been published externally. We are urgently investigating the nature and extent of the data that has been published. We apologise to our patients for any concern this latest development may cause.
To as best as possible safeguard our patients and our team, Genea has taken several steps ahead of and following the publication of this data …”
The company confirmed it was obtaining a “court-ordered injunction to prohibit any access, use, dissemination or publication of the impacted data by the threat actor and/or any third party who receives the stolen dataset”, was “working to understand precisely what data has been published and was “ensuring that our support package is available to those impacted by this incident. This includes the support of IDCARE, Australia’s national identity and cyber support community service”, and had notified the Office of the Australian Information Commissioner and the Australian Cyber Security Centre of the “latest development in this incident”.
Mary*, a Genea patient who spoke to news.com.au on the condition of anonymity and whose identity has been independently verified, said Genea wouldn’t answer questions about how non-ID data would be protected.

IDCare is a service that specialises in protection against identity fraud, but can’t do anything to protect sensitive medical data being leaked or misused.
As indicated, Genea has also sought an injunction in the NSW Supreme Court against “persons unknown” to make it clear that it’s illegal to access the data. The injunction was granted after the criminal hackers had listed the data for sale on the dark web.
Genea posted a “redacted” copy of the injunction to the website that this journalist was able to unredact by opening the automatically downloaded document in Preview on a Mac and simply deleting the boxes covering the sensitive information, including a link to the data on the dark web.
Mary, who brought this redacting error to our attention, told us that she felt this injunction likely only served to further spread the link to the stolen data, and that the poor effort in redacting did not give her confidence in Genea’s computer skills.
David Vaile, a cyber law expert and researcher in law and justice at UNSW, described the injunction as “hilarious” and “theatrical”.
Mr Vaile said that, even if the injunction had been properly redacted, cyber criminals were still likely to ignore it.
“I actually laughed when I saw that it’s directed to ‘persons unknown’. It’s basically an injunction to the world and they’re saying they can contact them if they want. It’s ludicrous. The problem with ransom is that it’s often carried out by very sophisticated actors and they are often offshore, out of the jurisdiction.”

Mr Vaile considered the injunction to be more of a PR move than an actual attempt to limit the spread of the stolen data.
While this Genea breach is breathtaking in its scope and the amount and types of data stolen, the OAIC statistics on notifiable data breaches show that healthcare providers are the most common targets for such attacks.
Between January and June 2024, there were 102 notifiable data breaches from health service providers, up significantly from the same period of the previous year. Because of this over-representation, some experts are calling for stronger protections for medical data, harsher penalties for negligence, and more scope for individuals to seek compensation from businesses when their data is improperly handled.
Australian Medical Association president Dr Danielle McMullen told news.com.au: “The AMA strongly advocates for a national data governance framework that protects patient privacy whilst ensuring health data is used ethically for improving care, not for commercial exploitation.”
Mr Vaile said: “Australian privacy law is notably and dramatically weak in terms of the capacity of individuals to enforce their rights compared to virtually any other developed country”.

He said that updates to privacy law in recent years have been “half-arsed” by government, remarking that the previous Coalition government tried to “do away with the notoriously underfunded privacy commissioner”, and then piled extra admin on the OAIC.
Professor Jha argues for more government support and guidance for healthcare companies to improve their cyber security.
One thing emphasised by almost all the experts we spoke to is that there is no way to prevent all data breaches. Data breaches are “inevitable”, but the important pillars of data security are holding only onto essential data, storing it as securely as possible, and notifying affected parties immediately because of how quickly these criminals move.
For those affected by this breach or any of the other medical data breaches, the OAIC suggests looking through the information and resources on the OAIC website. A Department of Home Affairs spokesperson said: “Data breaches that involve deeply personal information can be stressful for those impacted. Support is available at Head to Health if you need it – visit medicarementalhealth.gov.au”.
You can also contact Beyond Blue on 1300 22 4636.
*Name has been changed





