How AFP and FBI app AN0M works, and caught criminals in real time
The AFP and FBI secretly used an encrypted platform known as AN0M, to catch crims at their own game. This is how it operated.
National
Don't miss out on the headlines from National. Followed categories will be added to My News.
For almost three years, the AFP has been running an undercover investigation named Operation Ironside.
The AFP and FBI have secretly worked together on an encrypted platform known as AN0M, which was run by law enforcement, allowing us to see what criminals are planning in near real time.
The platform, sold on the black market, could send messages, distort voices or take videos – nothing else.
Only another person with the same app could receive communications.
This is how AN0M works and how police decrypted Australian criminals’ identities using it across the world.
THE HANDSET
A mobile phone stripped of most functions – it can’t make calls, look up maps, send emails or access internet. Uses a foreign SIM card to connect to Australian mobile networks, avoiding domestic laws requiring identification to obtain a mobile phone service. Can also be used over Wi-Fi. The platform began with a device solution that could scale quickly with resellers activating phones to the network. As demand grew so did the quality and type of handsets.
THE PURCHASE
Only available through underground criminal distributors and resellers. You had to be referred to a seller through an existing criminal user or be an existing acquaintance of a distributor who would vouch for you not being law enforcement. Handset and subscription packages cost between $1500 and $2500. Customers don’t have to reveal their name. Some paid in Bitcoin.
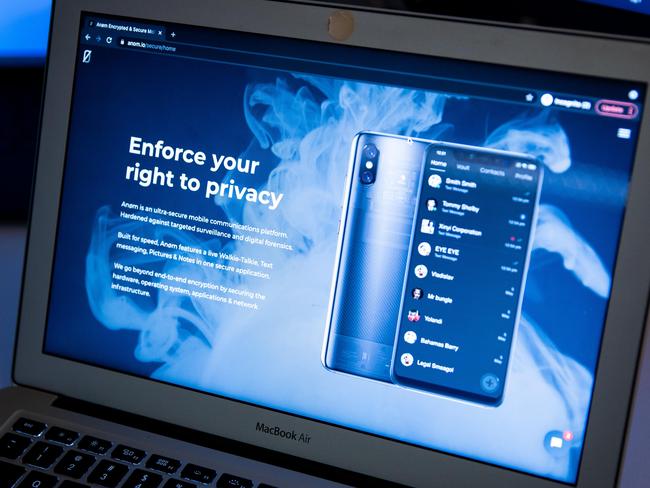
THE APP
Pre-loaded onto handsets and hidden behind a fully functional calculator icon. Criminals enter their pin or password into the calculator and the app opens. It offers end-to-end encryption, self-expiring messages, the capacity to take, pixelate and send photos to other users, voice distortion and secure file storage. Stealth mode enabled the handset to present as a normal mobile phone with bogus icons to look like normal apps and phone functions.

THE KILL SWITCH
A duress pin could be entered to wipe the device should the user be required by law enforcement to unlock the handset or asked for the password.
THE ARROGANCE
Crooks trusted the security of AN0M implicitly and used it to communicate openly about murder plots, retribution and violence on rival criminal groups or those that feel out of favour with them, massive drug deals and money laundering.
THE REALITY
Police were capturing text messages in real time and could undistort voice messages.
THE BOTS
Artificial Intelligence was built to constantly monitor and alert the AFP to identify words like “kill” and “kll”, translate foreign and coded communications and even determine whether the tone was serious or not.
THE MESSAGES
Millions of messages were being stored on secret law enforcement servers.
THE INSULT
The app was a ruse and criminals’ subscription fees were going directly into the pocket of law enforcement.

STEALTH MODE
The handset had the ability to enter a duress password to wipe the contents of the handset, as well as a stealth mode which disguised the handset as a regular phone (with bogus apps).
HOW POLICE FOUND CRIMINAL IDENTITIES ON AN0M
Police sometimes needed months to work out the true identity of the criminals behind the false names using the AN0M devices.
Establishing a person’s identity to a level that police were confident of – the process of attribution – was one of the vital cogs in the machinery of Operation Ironside.
With every user communicating under a false name or “handle’’, police were mostly unable to use traditional forensic techniques such as DNA and fingerprinting, and instead used digital detective skills to put names to devices.
Sometimes it was a matter of police surveillance teams eyeballing the person at a place where they had said they would be.

Due to the confidence users had in the supposed security of AN0M, some even sent photographs of themselves with the drugs they imported or in the process of committing acts of violence.
And police would “couple and compare’’ other sources of information to pin down a person’s true identity.
A senior team leader from Operation Ironside intelligence said this could involve drawing on information and intelligence from across police databases and other Commonwealth agencies and international partners.
“The time it took to attribute devices could sometimes become quite deflating, especially when you knew how significant they were. Some attributions could take hours, some days and some weeks … even months,’’ he said.

“Watching the team think they were close, then only to find out they were just off the mark … there was often profanity. But there were heaps of occasions watching the excitement of my team when they attributed devices. When they finally got their target, it was happy days and then onto the next handle.’’
An AFP spokesman said in the context of Operation Ironside, attribution meant establishing the true identity of the user of a specific device.
“Unlike regular mobile phones in Australia, subscriber details are not recorded for these devices, as the users consider their anonymity a paramount concern,’’ the spokesman said.
“As a result, we have to use other means to ascertain who is using each device.’’
He would not give details on how police established individual identities.
“We review all material collected against the device, to glean any insight we can into the user. These clues, coupled and compared with other sources of information, enable us to put a person to each device. Establishing the identity of the users is crucial to disrupting the criminal activity they facilitate using the devices,’’ he said.
Do you know more? Email us at crimeinvestigations@news.com.au
More Coverage
Originally published as How AFP and FBI app AN0M works, and caught criminals in real time





