Quantum Radiology cyber attack: Former and current employees data targeted
Staff of a western Sydney radiologist, hit by a cyber attack, were told to palm the data breach off as “an operational IT incident”, while also fielding harassing calls and texts from the hackers.

Penrith
Don't miss out on the headlines from Penrith. Followed categories will be added to My News.
Staff at a western Sydney radiologist
Imaging and diagnostics provider, Quantum Radiology, which operates 10 clinics across Sydney, including Nepean Radiology on High St, fell victim to a cyberattack on November 22, when an “unauthorised third party” breached the company’s IT system and “encrypted its contents” which included patients’ Medicare numbers, identifying information, claim details, image scans and reports.
A formal notification acknowledging the cyber attack was posted to Quantum’s website, which stated practitioners at each clinic had been informed and asked to assist in notifying patients.
The nature of the attack was also confirmed to staff in an email.
However an additional email sent internally in the days following instructed staff to tell patients there had been “an operational IT issue” under a set of directions headed “what to tell patients”.
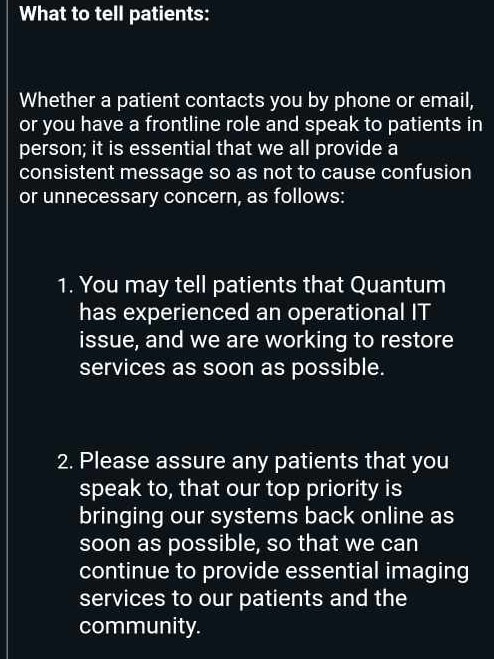
“You may tell patients that Quantum has experienced an operational IT issue and we are working to restore services as soon as possible,” the email said.
“If any patients ask for further details on the incident please let them know that we are working to return our systems to full functionality to minimise any impact to them.”
In a response to a question regarding what patients were told by staff, a spokesman for Quantum stated the formal notification posted online included “all relevant information”,
“We have published a formal notice on Quantum’s website which sets out relevant information about the incident and the services available to those affected, including the availability of a support centre for patients with cyber incident related queries.”
Hackers ‘harassing’ staff
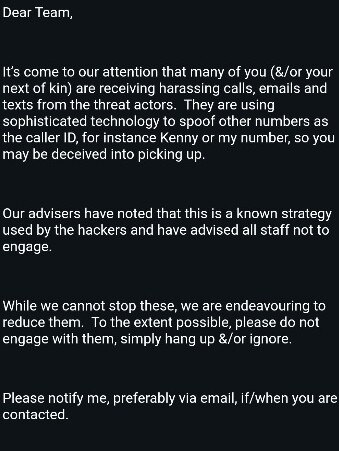
Another email circulated to staff acknowledged “threat actors” involved in the breach had been harassing workers with deceiving calls, emails and texts posing as managers within Quantum.
“It’s come to our attention that many of you /or your next of kin are receiving harassing calls, emails and texts from the threat actors, they are using sophisticated technology to spoof other numbers as the caller ID. so you may be deceived into picking up,” the email said

“Our advisers have noted this is a known strategy used by the hackers and have advised all staff not to engage, while we cannot stop them we are endeavouring to reduce them, please do not engage with them simply hang up or ignore.”
When approached for comment a spokesman for Quantum confirmed the “threat actor used illegal means to contact individuals associated with the company”.
“We are aware that the threat actor used illegal means to contact individuals associated with Quantum and we apologise for any concern that this may have caused at the time.”
Former and current employees targeted
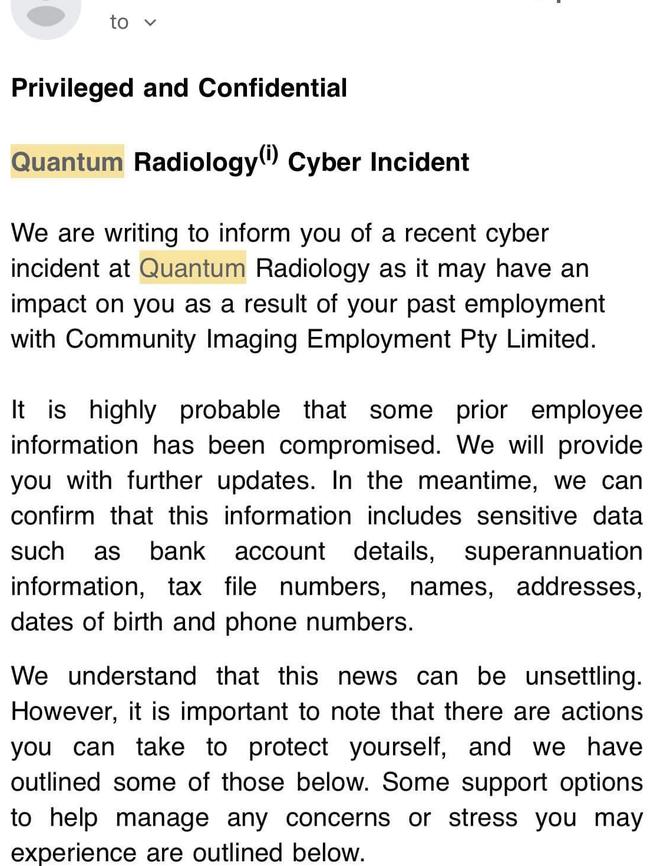
The Penrith Press can also reveal the personal information of both current and former employees were targeted in the attack, including bank account details, superannuation information, tax file numbers, names, addresses, dates of birth and phone numbers.
An email sent on November 30 warned former employees that it was “highly probable some prior employee information has been compromised”.
“We can confirm this information includes sensitive data such as bank account details, superannuation information, tax file numbers, names, addresses, dates of birth and phone numbers,” the message said.
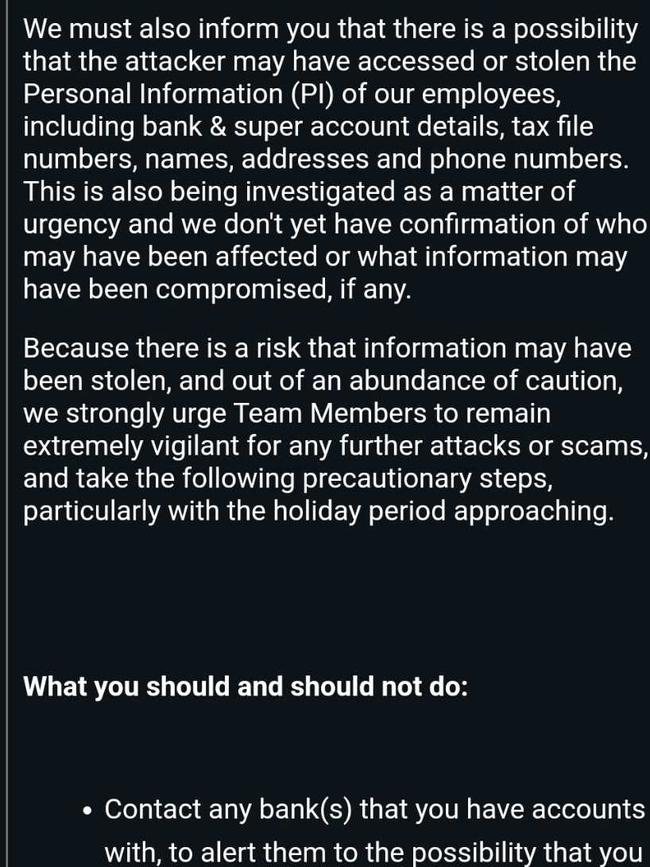
Current employees were told a full review was being taken into staff records, however at the time the email was sent “there was no evidence to suggest misuse of individuals data”.
Additionally Quantum offered their staff a 12-month subscription to fraud prevention software Equifax, as well as offering a step-by-step guide to protecting their information.
One former employee said she feared the sensitive nature of the data involved could leave her particularly vulnerable to identity theft.
“It's incredibly unsettling, we’re talking about everything they could possibly need to steal my identity and create a whole new me somewhere else,” she said
“It’s also frustrating because I worked there so long ago I can’t remember what details I did put down, so it’s hard to know exactly what I’m dealing with.”
When approached for comment a spokesman for Quantum said employees both past and present had been kept updated.
“We kept employees updated on the nature of the incident as our investigation evolved. We provided employees and former employees with steps they should take to protect themselves and services set up by Quantum to support them.” the statement said
No access to “historical data”
It comes as Quantum is still unable to access their historical databases six weeks after the incident.
When approached for comment a spokesman confirmed “we currently do not have access to our historical databases after being impacted by the cyber incident, but we are exploring multiple recovery options. We kindly ask that patients contact their referring doctors to access previous reports.”



