Why iPhone phishing scam shouldn’t become a problem
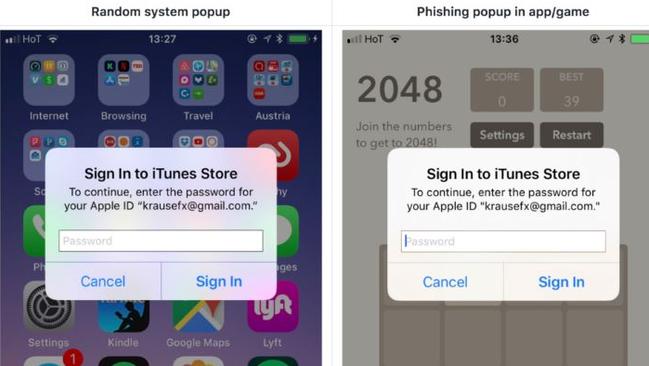
IT LOOKS exactly like a common iOS prompt but is designed to steal your password. But has Apple learned to snuff out these sneaky tricks?
Smartphone
Don't miss out on the headlines from Smartphone. Followed categories will be added to My News.
APPLE fans were warned about a hypothetical iPhone phishing attack by iOS code expert Felix Krause this week.
The phishing scam he designed mimics the familiar pop-up window on iOS devices which routinely prompts users to enter their Apple ID password when doing things like downloading apps. It looks exactly the same but it’s designed to steal your password.
The blog post gained major traction this week for showing the potential for hackers to make an easily deceptive iOS app feature, despite it not being in the wild.
“The goal of this blog post is to close the loophole that has been there for many years, and hasn’t been addressed yet,” Mr Krause wrote.
“For moral reasons, I decided not to include the actual source code of the pop-up, however it was shockingly easy to replicate the system dialogue.”
Apple declined to officially comment on the blog post but stressed the demonstration by Mr Krause remained a proof of concept and was not something currently being experienced by customers.
Ultimately a malicious developer would need to corrupt an app already in the app store or somehow sneak an app with malicious code past the auditing systems that scrutinise everything about a potential app — from its code to its appearance — before being approved to appear in the App Store.
Sebastian O’Halloran develops iOS apps under the moniker Juicy Apps in Hobart, Tasmania, and thinks these days such an app would almost certainly be detected by Apple.
The 18-year-old has been building apps since he was 11, and says he has experienced first hand just how finicky the company can be with its auditing process.
At 14 he designed an app to allow people with intellectual disabilities communicate what they wanted to get from the governments’ newly introduced disability care scheme.
Some of his apps have been rejected for relatively “minute” things in the past such as “mismatched screenshots” that didn’t appear to exactly match the appearance of the app’s interface.
“They’re incredibly thorough,” he told news.com.au. “They try to dismiss ‘scammy’ apps as much as possible.”
“In saying that there was a couple of apps that got through two or three years ago that were intended for scamming and somehow they got through the system.
“So I’m not saying it’s bullet proof.”
In 2013 researchers from the Georgia Institute of Technology found a way to sneak malicious iOS apps past Apple’s review process. Ultimately the apps could be updated after they’d been approved to carry out harmful actions without triggering security alarms. The researchers shared their successful act of deception in a paper titled: When Benign Apps Become Evil.
In 2015, hackers also managed to sneak malware designed to steal users’ iCloud passwords onto Chinese apps in the App Store.
These instances have no doubt caused Apple to bolster its review process — something which it clearly thinks would catch any app like the one made by Mr Krause.
Originally published as Why iPhone phishing scam shouldn’t become a problem



